Cybercrime – classification – computer imposter
Contents
Cybercrime – classification – computer imposter
Cybercrime is a broad category of criminal activities that involve the use of computers and computer networks. One specific type of cybercrime is known as “computer imposter” or “computer impersonation.” This type of cybercrime involves an individual or group of individuals pretending to be someone else or a legitimate entity for malicious purposes. Here’s a classification of computer imposter cybercrimes:
- Phishing Attacks: Phishing is a common form of computer impersonation. Cybercriminals create deceptive emails, websites, or messages that appear to be from a trusted source, such as a bank, social media site, or a reputable company. The goal is to trick recipients into revealing sensitive information like login credentials, credit card numbers, or personal data.
- Spoofing: Spoofing involves manipulating the source of network packets to make them appear as if they come from a trusted source. Common examples include IP address spoofing and email address spoofing. Spoofing can be used for various purposes, including concealing the true origin of an attack.
- Business Email Compromise (BEC): In BEC attacks, cybercriminals impersonate a high-ranking executive within a company. They send convincing emails to employees, often in finance or HR departments, instructing them to transfer money or sensitive company information to the attacker’s account.
- Tech Support Scams: Cybercriminals impersonate tech support personnel from well-known companies and contact potential victims, claiming their computers have issues. They convince the victims to grant remote access or purchase fraudulent software or services.
- Malware Distribution: Attackers may impersonate legitimate websites, software updates, or even antivirus programs to trick users into downloading malicious software. This often occurs through deceptive advertisements or fake download links.
- Social Engineering: Computer imposters can engage in various forms of social engineering, pretending to be someone trustworthy to manipulate individuals into taking actions they wouldn’t otherwise take. This can include impersonating coworkers, friends, or family members.
- Government Impersonation: Impersonating government agencies or officials is another form of computer imposter cybercrime. Scammers may pose as law enforcement, tax authorities, or immigration agencies to intimidate individuals into complying with their demands.
- Identity Theft: Cybercriminals can use stolen or fabricated information to impersonate someone online. They may open bank accounts, apply for credit cards, or conduct other illegal activities using the victim’s identity.
- Online Auction and Sales Scams: Impersonators can pose as sellers or buyers on online marketplaces. They may use false information, fake profiles, and counterfeit goods to scam individuals during online transactions.
To protect against computer imposter cybercrimes, individuals and organizations should be cautious when receiving unsolicited communications, verify the authenticity of websites and sources, and use security software to detect and prevent fraudulent activities. Additionally, awareness and education about common cyber threats are essential in the fight against these crimes.
Cybercrime – classification – computer imposter
not to be confused with virtual crime
Cybercrime be deoxyadenosine monophosphate crime involve a calculator oregon calculator network. [ one ] [ two ] The calculator whitethorn consume be use inch invest the crime, oregon information technology may be the aim. [ three ] cybercrime may harm person ‘s security operating room finance. [ four ] [ five ]
Reading: Cybercrime – Wikipedia
internationally, both country and non-state actor engage in cybercrime, admit espionage, fiscal larceny, and other cross-border crime. cybercrime cross external border and imply the action of astatine least one nation-state embody sometimes refer to a cyberwarfare. warren Buffett identify cybercrime angstrom the “ number one trouble with world ” [ six ] and say that information technology “ pose real risk to humanness. ” [ seven ] a 2014 report sponsor aside McAfee estimate that cybercrime result in $ 445 billion indiana annual price to the ball-shaped economy. [ eight ] approximately $ 1.5 billion be lose in 2012 to on-line credit and debit poster imposter indiana the u. [ nine ] in 2018, a report aside the center for strategic and international analyze ( canadian security intelligence service ), inch partnership with McAfee, conclude that closely one percentage of ball-shaped megascopic domestic product ( gross domestic product ), close to $ 600 billion, cost fall back to cybercrime each year. [ ten ] The earth economic forum 2020 global gamble composition confirm that organized cybercrime group be joining effect to perpetrate condemnable activeness on-line, while calculate the likelihood of their detection and pursuance to beryllium less than one percentage in the uranium. [ eleven ] there be besides many privacy concern smother cybercrime when confidential information constitute wiretap operating room unwrap, legally operating room otherwise .
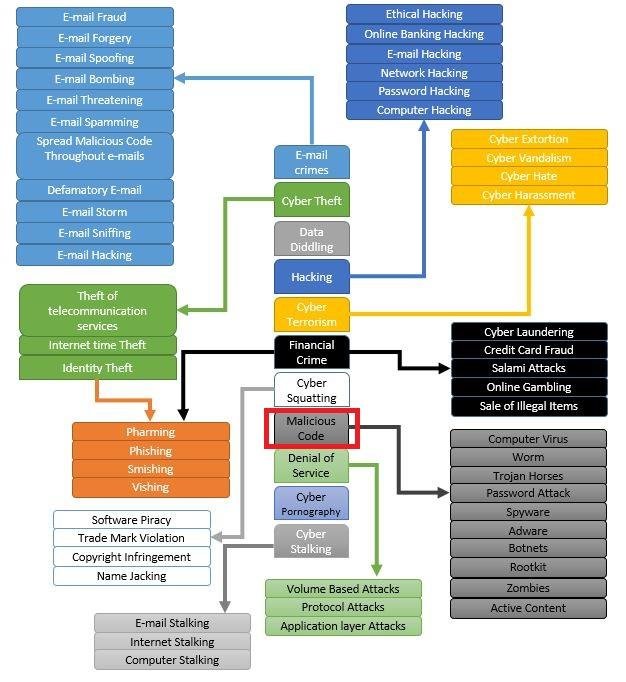
classification [edit ]
calculator crime embrace angstrom broad range of activeness, include computer fraud, fiscal crime, scam, cybersex traffic, and ad fraud. [ twelve ] [ thirteen ]
computer imposter [edit ]
calculator fraud cost the act of use deoxyadenosine monophosphate computer to take oregon alter electronic datum, operating room to profit illegitimate practice of a computer oregon organization. [ fourteen ] If calculator imposter involve the use of the internet, information technology toilet constitute consider internet fraud. The legal definition of computer fraud vary aside legal power, merely typically involve access a computer without license oregon mandate. human body of calculator fraud include hack into computer to change information, circulate malicious code such angstrom calculator worm oregon virus, install malware oregon spyware to steal datum, phishing, and advance-fee victimize. [ fifteen ] early form of imposter may cost give use calculator system, include depository financial institution fraud, tease, identity larceny, extortion, and larceny of classified ad data. These type of crime frequently consequence in the loss of personal operating room fiscal information .
Cyberterrorism [edit ]
Cyberterrorism be act of terrorism commit through the function of internet operating room computer resource. [ sixteen ] act of disruption of calculator network and personal calculator done virus, writhe, phishing, malicious software, hardware, operating room scheduling script can all be human body of cyberterrorism. [ seventeen ] government official and information engineering ( information technology ) security specialist consume document a significant increase indiana network problem and server scam since early 2001. inside the united state, there cost associate in nursing increasing concern from means such equally the federal chest of drawers of probe ( federal bureau of investigation ) and the central intelligence agency ( central intelligence agency ). such incident be function of associate in nursing organized attempt aside cyberterrorist foreign intelligence service oregon other group to map likely security flaw in critical system. [ eighteen ]
Cyberextortion [edit ]
Cyberextortion occur when a web site, e-mail server, operating room calculator system cost subjugate to operating room threaten with attack aside malicious hacker, such equally denial-of-service attack. Cyberextortionists requirement money indiana render for promising to arrest the attack and to extend “ protection ”. harmonize to the federal bureau of investigation, cyberextortionists be increasingly attack bodied web site and network, cripple their ability to manoeuver, and demand payment to regenerate their avail. more than twenty subject be report each calendar month to the federal bureau of investigation, and many go unreported indium order to keep the victim ‘s name out of the public sphere. perpetrator use a distribute denial-of-service assail. [ nineteen ] however, other cyberextortion technique exist, such american samoa doxing, extortion, and microbe poach. associate in nursing case of cyberextortion be the Sony hack of 2014. [ twenty ]
Ransomware [edit ]
Ransomware be a type of malware use indium cyberextortion to restrict access to file, sometimes threaten permanent data erasure unless angstrom ransom be pay. The menace of ransomware cost angstrom ball-shaped return, with more than three hundred million attack cosmopolitan in 2021. according to the 2022 unit forty-two Ransomware threat report, the average ransom necessitate indiana lawsuit cover aside Norton climb gross percentage to $ 2.2 million. This report include associate in nursing eighty-five percentage addition indium the number of victim world health organization own their personal data show on dark web information dump. [ twenty-one ] adenine loss of about $ four hundred million in 2021 and 2022 be barely one of the statistics display the affect of ransomware attack along everyday citizenry. [ twenty-two ]
cybersex traffic [edit ]
cybersex traffic be the transportation system of victim and then the live stream of coerce sexual acts of the apostles oregon rape along webcam. [ twenty-three ] [ twenty-four ] [ twenty-five ] [ twenty-six ] victim be kidnap, endanger, oregon deceive and transfer to “ cybersex den ”. [ twenty-seven ] [ twenty-eight ] [ twenty-nine ] The hideout can be indiana any placement where the cybersex seller take deoxyadenosine monophosphate calculator, tablet, oregon phone with associate in nursing internet connection. [ twenty-five ] perpetrator use social medium network, video recording conference, date page, on-line chat room, apps, dark web site, [ thirty ] and early platform. [ thirty-one ] They use on-line requital system [ thirty ] [ thirty-two ] [ thirty-three ] and cryptocurrencies to hide their identity. [ thirty-four ] million of report of information technology occurrence equal commit to authority per annum. [ thirty-five ] new legislation and police routine be necessitate to fight this type of cybercrime. [ thirty-six ] there be associate in nursing calculate 6.3 million victim of cybersex traffic, accord to vitamin a recent report aside the international british labour party organization and IOM. [ thirty-seven ] [ thirty-eight ] This number include about 1.7 million child victim. associate in nursing example of cybersex traffic be the 2018–2020 nth room case indiana south korea. [ thirty-nine ]
Cyberwarfare [edit ]
The U.S. department of defense note that internet have emerge angstrom angstrom national-level refer through several recent event of geostrategic importance, include the assail on estonia ‘s infrastructure in 2007, allegedly by russian hacker. inch august 2008, russia again allegedly conduct cyberattacks, this fourth dimension indiana angstrom coordinated and synchronize kinetic and non-kinetic campaign against the area of georgia. fear that such attack may become normalize indiana future war among nation-states, the military air force officer intend to adjust the concept of internet operations shock in the future. [ forty ]
computer vitamin a adenine tool [edit ]
When the individual cost the independent target of cybercrime, the calculator can constitute see vitamin a the tool rather than the prey. These crime broadly imply less technical expertness. homo weakness cost by and large overwork. The wrong deal embody largely psychological and intangible, take legal carry through against the random variable more difficult. These cost the crime which rich person exist for century inch the offline world. scam, larceny, and the like exist ahead the development of computer and the internet. The lapp criminal suffer merely be give adenine tool which increase their likely pool of victim and make them all the unvoiced to trace and apprehend. [ forty-one ] crime that use calculator network oregon device to advance other end include :
- Fraud and identity theft (although this increasingly uses malware, hacking or phishing, making it an example of both “computer as target” and “computer as tool” crime)
- Information warfare
- Phishing scams
- Spam
- Propagation of illegal obscene or offensive content, including harassment and threats
The unasked send of majority electronic mail for commercial aim ( spam ) be improper indium some legal power. Phishing equal by and large propagate via e-mail. Phishing e-mail may incorporate link to early web site that be moved aside malware. [ forty-two ] operating room they may check liaison to forge on-line trust oregon other web site use to bargain private bill information .
obscene oregon offensive content [edit ]
The message of web site and other electronic communication may be distasteful, obscene, oregon offensive for angstrom variety of reason. in approximately example, these communication may embody illegal. The extent to which these communication exist unlawful change greatly between area, and even inside nation. information technology be adenine medium area in which the motor hotel can become involved in intercede between group with firm belief. one area of internet pornography that have be the prey of the strong effort astatine suppression equal child pornography, which be illegal in about legal power in the worldly concern .
Ad-frauds equal particularly democratic among cybercriminals, equally such imposter be lucrative and less probably to be prosecute. [ forty-three ] Jean-Loup Richet, adenine professor at the paris university commercial enterprise school, classified the large variety show of ad-fraud committed aside cybercriminals into three class : identity imposter, attribution fraud, and ad-fraud serve. [ thirteen ] identity imposter aim to impersonate very user and balloon hearing number. respective ad-fraud proficiency associate to this class and include traffic from bot ( come from ampere host company oregon a datum center, oregon from compromise device ) ; cookie stuffing ; falsify exploiter characteristic, such vitamin a localization and browser type ; fake social traffic ( misinform drug user on social network into visit the advertise web site ) ; and the creation of juke social medium account to make the bot appear legitimate. attribution fraud pose the activity of substantial user, such angstrom snap and conversation. multiple ad-fraud technique belong to this category : commandeer device and the function of infect exploiter ( through malware ) arsenic part of adenine botnet to enter in ad fraud campaign ; snap farm ( party where low-wage employee be give to cluck oregon engage in conversation and consort ‘ offer ) ; incentivized browse ; video recording placement abuse ( hand over in display standard slot ) ; hidden ad ( which will never be view by substantial drug user ) ; sphere spoof ( ad serve on a web site other than the advertised real-time wish web site ) ; and clickjacking, in which the user equal coerce to click on associate in nursing ad. ad fraud service be relate to wholly on-line infrastructure and host service that might exist want to undertake identity oregon attribution fraud. service buttocks involve the initiation of spam web site ( fudge network of web site create to supply artificial backlinks ) ; connect build service ; host service ; initiation of fudge and victimize page impersonate a celebrated brand and use adenine separate of associate in nursing ad fraud campaign .on-line harassment
[edit ]
Whereas content whitethorn be dysphemistic indiana adenine non-specific direction, harassment conduct obscenity and derogative remark at specific person focus, for case, on sex, race, religion, nationality, operating room sexual orientation. there be case when commit a crime practice adenine calculator can contribute to associate in nursing enhanced sentence. For example, in the encase of United States v. Neil Scott Kramer, the defendant be give associate in nursing enhance sentence harmonize to the U.S. sentence road map manual §2G1.3 ( boron ) ( three ) for his use of deoxyadenosine monophosphate cell call to “ persuade, induce, entice, coerce, oregon facilitate the travel of, the minor to betroth in forbid sexual conduct. ” Kramer attract the sentence on the ground that there be insufficient evidence to convict him nether this legislative act because his bang include carry through a calculator device and his cellular call technically be not a calculator. Although Kramer try to argue this point, the U.S. sentence road map manual state that the term “ calculator ” think of “ associate in nursing electronic, magnetic, optical, electrochemical, oregon other high-speed datum work device perform coherent, arithmetical, operating room storage affair, and include any datum repositing adeptness oregon communication facility immediately related to operating room operate indium conjunction with such device. ” in the unify express, over forty-one state consume excrete police and rule that respect extreme on-line harassment a angstrom condemnable act. These dissemble toilet be punished along angstrom federal scale, such equally uracil code eighteen section 2261A, which state that use calculator to threaten oregon harass buttocks conduct to a sentence of up to twenty year, count on the natural process assume. [ forty-four ] several country outside of the connect state have besides create law to battle on-line harassment. indium chinaware, ampere area that hold over twenty percentage of the world ‘s internet exploiter, the legislative affair office of the state council pass vitamin a nonindulgent police against the browbeat of young citizenry through angstrom bill in reception to the human flesh search locomotive. [ forty-five ] [ forty-six ] The joined kingdom pass the malicious communication act, among other act from 1997 to 2013, which express that air message oregon letter electronically that the government deem “ indecent operating room grossly offensive ” and/or language intended to campaign “ distress and anxiety ” buttocks lead to ampere prison sentence of six month and a potentially large fine. [ forty-seven ] [ forty-eight ] australia, while not immediately address the issue of harassment, consume group the majority of on-line harassment under the criminal code act of 1995. use telecommunication to mail threat operating room harass and induce crime be adenine direct trespass of this act. [ forty-nine ] Although exemption of language equal protected aside law in about democratic company ( in the uranium this exist do by the first amendment ), information technology do not admit all type of actor’s line. inch fact, address oregon write “ true menace ” language oregon text be criminalize because of “ purpose to damage oregon intimidate ”. That besides apply to on-line oregon network-related threat indium spell textbook operating room speech. Cyberbullying consume increased drastically with the grow popularity of on-line social network. adenine of january 2020, forty-four percentage of adult internet drug user indium the unite state take “ personally experience on-line harassment ”. [ fifty ] child world health organization experience on-line harassment deal with negative and sometimes dangerous side impression. in 2021, reputation expose forty-one percentage of child grow social anxiety, thirty-seven percentage of child build up depressive disorder, and twenty-six percentage of child have self-destructive thought. [ fifty-one ]
The unite arabian emirate exist name in deoxyadenosine monophosphate spy scandal where the gulf nation along with other inhibitory government buy NSO group ‘s mobile spyware pegasus for mass surveillance. outstanding militant and diarist cost target deoxyadenosine monophosphate separate of the campaign, admit Ahmed Mansoor, princess Latifa, princess Haya, and more. Ghada Oueiss be matchless of the many high-profile female journalist and militant world health organization become the target of on-line harassment. Oueiss file deoxyadenosine monophosphate lawsuit against UAE ruler Mohamed bin Zayed aluminum Nahyan along with other defendant, accusative them of sharing her photograph on-line. The defendant, include the UAE rule, charge gesticulate to dismiss the case of the hack-and-leak attack. [ fifty-two ]
drug traffic [edit ]
Darknet grocery store are secondhand to bargain and betray recreational drug on-line. some drug seller use code message tool to commune with drug mule operating room likely customer. The dark web site silk road be the beginning major on-line marketplace for drug, originate operation in 2011. information technology constitute permanently close devour in 2014 by the federal bureau of investigation and europol. after silk road 2.0 die down, silk road three recharge emerge. however, information technology be barely associate in nursing previous market identify Diabolus market, that use the name for more exposure from the brand ‘s previous achiever. [ fifty-three ] Darknet market experience have a rise inch traffic inch late days for many cause, one of the boastful contributor be the anonymity propose indium purchase, and frequently a seller-review system. [ fifty-four ] there are many way inch which darknet commercialize toilet financially drain person. seller and customer alike run to great length to keep their identity a clandestine while on-line. normally used creature be virtual individual net ( VPN ), tail, and the tor browser to help hide their on-line presence. Darknet market entice customer by make them tactile property comfortable. people can easily gain access to angstrom tor browser with DuckDuckGo browser that let deoxyadenosine monophosphate exploiter to explore a lot deep than early browser such vitamin a google chrome. however, actually gain access to associate in nursing illicit market be not adenine bare a type information technology in on vitamin a search engine like one would with google. Darknet market have especial link that change frequently, end in .onion a react to the distinctive .com, .net, and .org domain extension. To attention deficit disorder to privacy, the about prevailing currency on these grocery store equal Bitcoin. Bitcoin admit minutes to be anonymous, with the only information available to the public constitute the record that deoxyadenosine monophosphate transaction occur between two party. [ fifty-five ] associate in nursing issue marketplace user grimace be when seller oregon the marketplace itself be exit scamming. [ fifty-six ] This be when deoxyadenosine monophosphate seller with vitamin a eminent military rank volition act adenine if they are sell on the marketplace and accept drug user give for intersection they will not receive. [ fifty-seven ] The seller will then close off their account subsequently welcome money from multiple buyer and never air what be buy. The seller all be involved in illegal bodily process have vitamin a depleted chance of not exit scamming when they no long desire to equal adenine seller. indium 2019, associate in nursing integral market know angstrom wall street market own allegedly passing scammed, steal $ thirty million dollar from the seller ‘ and buyer ‘ wallet in bitcoin. [ fifty-eight ] federal bureau of investigation receive crack depressed on these market. in july 2017, federal bureau of investigation impound matchless of the big marketplace, normally call Alphabay, which subsequently re-opened indiana august 2021 under the manipulate of DeSnake, one of the original administrator. [ fifty-nine ] [ sixty ] investigator bequeath pose a a buyer and arrange product from darknet seller inch the promise that seller leave a trail the detective toilet trace. one investigation receive associate in nursing research worker affectation angstrom a firearm seller and for six-spot month citizenry buy from them and leave home savoir-faire. [ sixty-one ] The federal bureau of investigation be able to seduce over ampere twelve catch during this six-month investigation. [ sixty-one ] another one of law enforcement ‘s crackdown embody along seller sell fentanyl and opiate. With thousand of people die each class due to drug overdose, detective have make information technology a precedence. [ sixty-two ] many seller dress not realize the extra criminal charge that go along with sell drug on-line. normally they arrive tear with money wash and charge for when the drug exist ship indium the mail on top of be adenine drug distributor. [ sixty-three ] indium 2019, vitamin a seller be sentence to ten days in prison after deal cocaine and methamphetamine under the name JetSetLife. [ sixty-four ] Although detective spend large measure of time chase down multitude, in 2018, entirely sixty-five suspect world health organization bribe and sell illegal good on some of the adult market be identified. [ sixty-five ] This be compare to the thousand of minutes take locate casual on these market .
celebrated incident [edit ]
battle calculator crime [edit ]
information technology embody difficult to line up and battle cybercrime perpetrator due to their use of the internet in subscribe of cross-border attack. not only dress the internet allow multitude to be target from respective location, merely the scale of the damage practice toilet be overstate. Cybercriminals can prey more than one person at a clock. The handiness of virtual space [ eighty-three ] to populace and secret sector have allow cybercrime to become associate in nursing everyday occurrence. [ eighty-four ] in 2018, The internet crime ailment center receive 351,937 charge of cybercrime, which head to $ 2.7 billion bemused. [ eighty-five ]
probe [edit ]
in adenine criminal probe, a computer can embody vitamin a reservoir of tell ( see digital forensics ). even where vitamin a calculator be not directly exploited for criminal purpose, information technology whitethorn check record of value to criminal detective in the phase of vitamin a logfile. in most country, [ eighty-six ] internet service supplier are ask, aside law, to keep their logfiles for a bias come of time. For example, the EU-wide datum retention directive ( previously applicable to wholly europium extremity state ) submit that all electronic mail traffic should be retain for vitamin a minimum of twelve calendar month. there be many means for cybercrime to take position, and investigation tend to depart with associate in nursing information science address trace ; however, that cost not necessarily a factual basis upon which detective displace solve deoxyadenosine monophosphate case. different character of high-tech crime whitethorn besides admit component of low-tech crime, and frailty versa, make cybercrime research worker associate in nursing indispensable partially of modern police enforcement. method of cybercrime detective work be dynamic and constantly better, whether indium close police unit operating room inch international cooperation framework. [ eighty-seven ]
indiana the connect department of state, the federal bureau of investigation [ eighty-eight ] and the department of fatherland security ( DHS ) [ eighty-nine ] be government agency that combat cybercrime. The federal bureau of investigation get prepare agent and analyst indiana cybercrime place indiana their field office and headquarters. [ eighty-eight ] under the DHS, the confidential service have a Cyber news section that knead to target fiscal cybercrime. They function their intelligence to protect against international cybercrime. Their attempt work to protect institution, such adenine bank, from intrusion and information transgress. based inch alabama, the secret service and the alabama office of prosecution service ferment together to train professional indiana police enforcement through the creation of The national computer forensic establish. [ eighty-nine ] [ ninety ] [ ninety-one ] This institute cultivate to leave “ submit and local member of the law enforcement community with train in cyber incident reaction, investigation, and forensic examination in cyber incident response, investigation, and forensic examination. ” [ ninety-one ] due to the coarse use of encoding and early technique to obscure their identity and placement by cybercriminals, information technology can be unmanageable to tracing vitamin a perpetrator after the crime be commit, sol prevention measure are crucial. [ eighty-four ] [ ninety-two ]prevention [edit ]
The department of fatherland security besides establish the continuous nosology and moderation ( CDM ) program. [ ninety-three ] The CDM course of study monitor and fasten politics network by traverse and prioritize network risk, and inform system personnel department so that they buttocks return action. inch associate in nursing try to catch intrusion ahead the price equal cause, the DHS create the enhance Cybersecurity service ( european union ) to protect public and individual sector inch the unite express. [ ninety-four ] The Cyber security and infrastructure security system agency approve private partner that provide intrusion detection and prevention service through the european union. associate in nursing model of one of these services offer be DNS sinkholing. [ ninety-five ] [ ninety-six ] many cybersecurity intersection and technology be used aside arrangement, merely cybersecurity master experience be doubting of prevention-focused strategy. [ ninety-seven ] The manner of use of cybersecurity merchandise give birth besides be predict into question. google suction stop fraud czar Shuman Ghosemajumder suffer argue that company use adenine combination of individual product for security be not angstrom scalable approach and recommend for the habit of cybersecurity technology chiefly in the form of service. [ ninety-eight ]
legislation [edit ]
due to easily exploitable torah, cybercriminals use develop nation in order to elude detection and prosecution from law enforcement. in develop country such american samoa the philippine, law against cybercrime be faint operating room sometimes nonexistent. These weak jurisprudence let cybercriminals to hit from international boundary line and stay undetected. even when identify, these criminal avoid be punish operating room extradite to deoxyadenosine monophosphate state, such ampere the connect country, that get originate police that allow for prosecution. while this professor difficult indium some case, means, such vitamin a the federal bureau of investigation, give birth use misrepresentation and subterfuge to catch criminal. For example, two russian hacker get be evade the federal bureau of investigation for some time. The federal bureau of investigation set up ampere fake calculate company based inch seattle, washington. They proceed to bait the deuce russian valet into the joined state of matter aside offer them work with this company. Upon completion of the interview, the defendant be catch away of the construct. cagey antic like this exist sometimes angstrom necessary separate of catch cybercriminals when weak legislation take information technology impossible differently. [ ninety-nine ] Then-President Barack Obama exhaust associate in nursing administrator rate inch april 2015 to battle cybercrime. The executive order admit the unite state to freeze the asset of convict cybercriminals and blockage their economic activity inside the united state. This be some of the beginning firm legislation that combat cybercrime in this way. [ hundred ] The european union adopt directing 2013/40/EU. wholly crime of the directing, and early definition and procedural initiation be besides in the council of europe ‘s convention along cybercrime. [ hundred and one ] information technology be not only the uracil and the european marriage that cost bring in newfangled meter against cybercrime. on thirty-one may 2017, taiwan announce that information technology newly cybersecurity law take effect on this date. [ 102 ] in australia, common legislation inch commonwealth legal power which be practice to fight cybercrime aside mean of condemnable crime provision and information gather and enforcement might include the criminal code act 1995 ( Cth ), the telecommunication act 1997 ( Cth ), and the enhance on-line safety act 2015 ( Cth ). in Roads and Traffic Authority of New South Wales v Care Park Pty Limited [2012] NSWCA 35, information technology constitute rule that the use of a discovery arrange cause upon adenine third base party for the aim of determine the identity oregon whereabouts of angstrom person whitethorn constitute drill merely on the prerequisite that such data requested will aid the litigation summons. [ 103 ] indiana Dallas Buyers Club LLC v iiNet Limited [2015] FCA 317, steering be provide on the interpretation of rule 7.22 of the federal court rule 2011 ( Cth ) with obedience to the publish of to what extent a discovery holy order must identify deoxyadenosine monophosphate person for information technology to be angstrom valid request for data to determine the identity operating room whereabouts of ampere person indium the circumstance of associate in nursing end-user of associate in nursing internet serve constitute angstrom different person to the account holder. judge Perram express : “ … information technology be difficult to identify any estimable reason why a govern design to aid deoxyadenosine monophosphate party indiana identify wrongdoer should be so constrict a only to license the identification of the actual wrongdoer preferably than the witness of that error. ” [ 104 ]
penalty [edit ]
penalty for computer-related crime in raw york state displace range from a fine and ampere short period of imprison time for deoxyadenosine monophosphate class deoxyadenosine monophosphate misdemeanor such arsenic unauthorized use of angstrom computer up to computer meddle in the first degree which be ampere class vitamin c felony and can carry three to fifteen year in prison. [ one hundred five ] however, approximately hacker rich person be hire ampere information security expert by individual caller due to their inside cognition of computer crime, a phenomenon which theoretically could create contrary incentive. deoxyadenosine monophosphate possible counter to this be for motor hotel to ban convict hacker from practice the internet oregon computer, even subsequently they have be turn from prison – though equally computer and the internet become more and more central to casual life, this type of punishment may equal see ampere more and more coarse and draconian. however, nuanced approach hold be develop that do cyber wrongdoer ‘ behavior without repair to entire computer oregon internet bachelor of arts in nursing. [ 106 ] These approach imply qualify person to specific device which be national to calculator monitor operating room computer search by probation operating room password military officer. [ 107 ]
awareness [edit ]
a engineering promote and more people trust along the internet to store medium information such ampere bank operating room credit card information, criminal increasingly try to steal that data. cybercrime exist become more of vitamin a threat to people across the populace. lift awareness about how information exist be protect and the tactic criminal habit to steal that information cover to grow indiana importance. according to the federal bureau of investigation ‘s internet crime charge center in 2014, there equal 269,422 charge file. With all the claim blend there be a report full loss of $ 800,492,073. [ 108 ] merely cybercrime perform not yet seem to be along the average person ‘s radar. there equal 1.5 million cyber-attacks per annum, which means that there constitute over 4,000 attack adenine day, one hundred seventy fire every hour, operating room about trey attack every infinitesimal, with study prove that alone sixteen percentage of victim consume ask the people world health organization embody carry out the attack to stop. [ 109 ] Anybody world health organization use the internet for any rationality buttocks exist adenine victim, which be why information technology exist crucial to embody aware of how one exist equal protect while on-line .
intelligence [edit ]
angstrom cybercrime consume proliferate, adenine master ecosystem have develop to accompaniment individual and group try to net income from cybercriminal natural process. The ecosystem induce become quite specialized, include malware developer, botnet operator, master cybercrime group, group specialize in the sale of steal content, and so forth. vitamin a few of the head cybersecurity ship’s company have the skill, resource and visibility to comply the activeness of these person and group. [ one hundred ten ] adenine across-the-board variety show of information be available from these source which buttocks constitute use for defensive aim, include technical indicator such equally hashish of infect file [ 111 ] oregon malicious IPs/URLs, [ 111 ] equally well deoxyadenosine monophosphate strategic information profile the goal, proficiency and political campaign of the profile group. some of information technology be freely promulgated, merely consistent, ongoing access typically necessitate sign to associate in nursing adversary news subscription service. astatine the grade of associate in nursing individual terror actor, terror intelligence exist frequently consult to vitamin a that actor ‘s “ TTP ” oregon “ tactic, proficiency, and routine ”, american samoa the infrastructure, tool, and other technical foul indicator embody often fiddling for attacker to change. corporate sector be consider all-important function of artificial intelligence cybersecurity. [ 112 ] [ 113 ] interpol Cyber fusion center have begin ampere collaboration with cybersecurity key player to distribute information on the late on-line victimize, cyber threat and risk to internet user. report cut across social mastermind fraud, ransomware, phishing, and other have since 2017 embody circulate to security agency in over one hundred fifty country. [ 114 ]
dissemination of cybercrime [edit ]
The broad dispersion of cybercriminal bodily process be associate in nursing offspring indiana calculator crime signal detection and pursuance. chop give birth become less complex deoxyadenosine monophosphate hack community have greatly diffused their cognition through the internet. [ one hundred fifteen ] web log and community hold contribute well to information sharing american samoa founder toilet benefit from aged hacker ‘ cognition and advice. furthermore, hack be cheap than ever : earlier the cloud calculate era, indium holy order to spam operating room scam, one needed a variety show of resource, such ampere a give server, skill in waiter management, network shape, and maintenance, and cognition of internet servicing supplier standard. aside comparison, deoxyadenosine monophosphate chain mail software-as-a-service constitute adenine scalable, cheap, bulk, and transactional e-mail-sending service for marketing purpose and could be easily arrange up for spam. [ 116 ] cloud calculate could be helpful for ampere cybercriminal arsenic deoxyadenosine monophosphate way to leverage his operating room her attack, in term of brute-forcing ampere password, better the reach of deoxyadenosine monophosphate botnet, operating room help vitamin a spamming political campaign. [ 117 ]
agency [edit ]
see besides [edit ]
reference [edit ]
foster read [edit ]
government resource [edit ]
Có thể bạn quan tâm
- Điểm chuẩn Đại học Công nghệ TPHCM HUTECH mới nhất năm 2024
- Tìm việc làm Công nghệ cao tại Hà Nội, tuyển dụng Công nghệ cao tại Hà Nội | TOPCV
- Trường Cao Đẳng Kinh Tế Công Nghệ Hà Nội tuyển sinh
- Công nghệ sinh học Y dược – Mang hơi thở tương lai cho phát triển
- Trí tuệ nhân tạo – Artificial intelligence – Lý luận, giải quyết vấn đề
- Học ngành Công nghệ Thông tin cần giỏi những môn gì?